Scanning for Trouble: A Guide to Vulnerability Management Process
With the increasing frequency and complexity of cyber-attacks, businesses must have a solid security plan in place to protect their sensitive information and assets. One crucial aspect of this plan is the Vulnerability Management process, which involves identifying and addressing potential security weaknesses in your systems before they can be exploited by cybercriminals.
In this blog post, we’ll explain why Vulnerability Management is crucial for your organization’s security and how you can implement an effective Vulnerability Management process. We will also highlight some key benefits of Vulnerability Management, including improved threat detection and response, enhanced compliance, and better risk management. So, if you want to ensure the security of your business, keep reading!
What is Vulnerability Management?
It is like flossing for your computer systems. Just like flossing helps remove the gunk between your teeth, vulnerability management helps you identify and address potential weaknesses in your systems before they can be exploited by cybercriminals. In other words, it’s a way to keep your systems healthy and happy!
Different stages of vulnerability management
The vulnerability management process can be broken down into three stages: vulnerability scanning, analysis, and remediation. It’s kind of like a doctor’s visit – first, you get checked up, then the doctor analyzes the results, and finally, you get prescribed a treatment plan.
During the vulnerability scanning stage, you’re basically checking your system for any signs of trouble. It’s like a TSA checkpoint for your digital assets – you want to make sure there’s nothing suspicious going on.
Once you’ve identified any potential vulnerabilities, it’s time for the analysis stage. This is where you figure out what the heck is going on and how to fix it. It’s like a detective solving a crime – you need to gather all the evidence and piece together the puzzle.
Finally, in the remediation stage, you get to put your plan into action and fix those vulnerabilities once and for all. It’s like a superhero coming in to save the day – you’re swooping in to save your systems from the bad guys.
Why is Vulnerability Management Important?
Risks of cyber-attacks and data breaches
If you’ve ever seen a heist movie, you know that thieves are always looking for vulnerabilities to exploit. Cybercriminals are no different – they’re always on the lookout for weaknesses in your system that they can use to steal your data or wreak havoc on your business. It’s like the Wild West out there, and your digital assets are gold.
How vulnerability management can help protect your business and its assets
Thankfully, vulnerability management is like the sheriff in town – it’s there to protect your systems and assets from those pesky cyber criminals. By regularly scanning your systems for vulnerabilities and addressing them promptly, you’re making it much harder for cybercriminals to do their dirty work. It’s like building a fortress around your digital assets – no thief wants to mess with that.
Potential consequences of not having a vulnerability management process in place
Not having a vulnerability management process in place is like leaving your front door unlocked and your valuables out in the open. You’re practically inviting cybercriminals to come and help themselves. And trust us, you don’t want that. The consequences of a cyber-attack can be devastating – from financial loss to damage to your reputation. It’s like a tornado ripping through your business – it can leave a trail of destruction in its wake.
So, if you want to keep your business safe and sound, make sure you have a solid vulnerability management plan in place. It’s like having your very own sheriff in town – and trust us, you want that.
Implementing an Effective Vulnerability Management Process
Steps involved in implementing a vulnerability management process
Implementing a vulnerability management process is kind of like cooking a fancy meal – it takes some time and effort, but the end result is totally worth it. The first step is to figure out what you want to cook (or, in this case, what assets you want to protect). Then, you need to gather all the ingredients (aka vulnerability management tools). Once you have everything you need, it’s time to get cooking (or scanning, analyzing, and remedying, in this case).
Tips for selecting the right vulnerability management tools and solutions
Selecting the right vulnerability management tools is like picking the perfect spice blend for your dish – it can make or break the flavor. You want to make sure you’re selecting tools that are effective, user-friendly, and fit within your budget. It’s like going to the grocery store – you don’t want to overspend on fancy ingredients that you don’t really need.
How to prioritize vulnerabilities and allocate resources efficiently
Prioritizing vulnerabilities and allocating resources efficiently is like hosting a dinner party – you want to make sure everyone is happy and satisfied. In this case, you want to make sure you’re addressing the most critical vulnerabilities first (the guests of honor, if you will) and allocating resources in a way that makes the most sense for your business. It’s like figuring out the seating chart – you want to make sure everyone is sitting in the right spot to have a good time.
Implementing an effective vulnerability management process is essential for any business that wants to stay safe and secure. So, grab your apron (or your vulnerability management tools) and get cooking (or scanning, analyzing, and remedying)!
How vulnerability management can improve your organization’s security posture
Improving your organization’s security posture is like getting a flu shot – you’re less likely to get sick, and if you do get sick, your symptoms will be less severe. Similarly, vulnerability management helps prevent cyber-attacks and data breaches, making it much harder for cybercriminals to do their dirty work. It’s like putting up a shield around your organization – no attacker wants to mess with that.
Benefits of vulnerability management
The benefits of vulnerability management are like winning the lottery – you get a whole bunch of good stuff all at once. Improved threat detection and response mean you’re able to quickly identify and address potential security threats. Enhanced compliance means you’re meeting all the necessary security requirements (and who doesn’t love meeting requirements?). And better risk management means you’re able to make more informed decisions about how to allocate resources and prioritize security efforts. It’s like having a superpower – you’re able to see and do things that others can’t.
So, if you want to be a superhero in the cybersecurity world, make sure you’re taking advantage of all the benefits of vulnerability management. It’s like having a secret weapon – and trust us, you want that.
Best Practices for Vulnerability Management
Following best practices for vulnerability management is like following a recipe for the perfect batch of cookies – it ensures that everything turns out just right. Regular vulnerability assessments are like checking the oven temperature – you want to make sure everything is cooking evenly. Employee training is like measuring out the ingredients – you want to make sure everyone knows what they’re doing. And continuous monitoring is like keeping an eye on the cookies as they bake – you don’t want them to burn.
How to create a culture of security within your organization
Creating a culture of security within your organization is like getting your whole family to eat their vegetables – it might take some convincing, but it’s totally worth it in the end. You want to make sure everyone understands the importance of cybersecurity and is committed to following best practices. It’s like convincing your kids that broccoli is actually delicious (spoiler alert: it is).
The Steps Involved in the Vulnerability Management Process
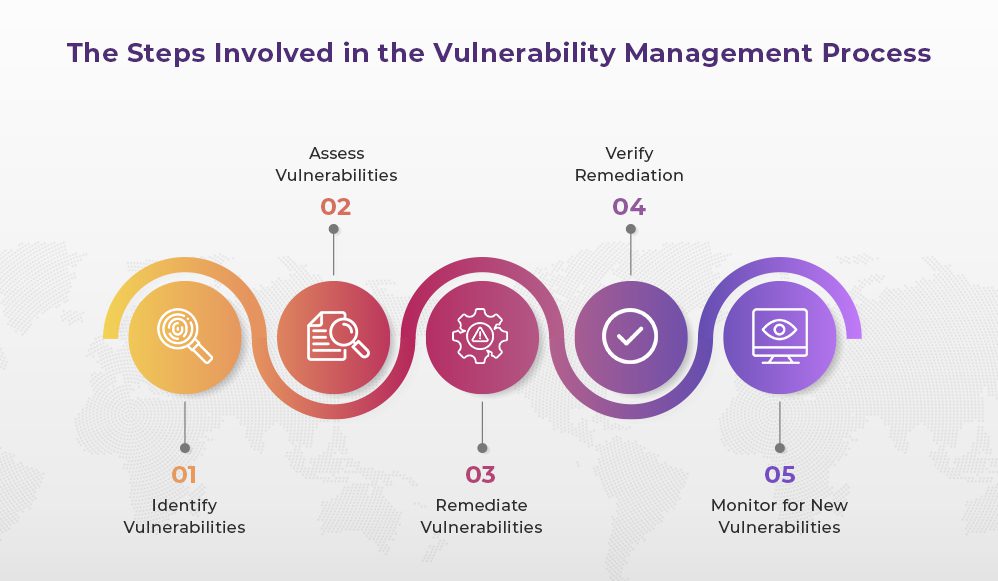
The vulnerability management process is like playing a game of whack-a-mole – you’re constantly identifying and fixing new vulnerabilities as they pop up. Here are the basic steps involved in the process:
- Identify vulnerabilities: This is like spotting the moles as they pop up – you want to make sure you’re aware of all the potential vulnerabilities in your system. It’s like playing Where’s Waldo, but instead of finding a guy in a striped shirt, you’re finding potential security holes in your system.
- Assess vulnerabilities: This is like deciding which mole to whack first – you want to prioritize the vulnerabilities based on their severity and potential impact. It’s like deciding which mole is the biggest threat to your high score.
- Remediate vulnerabilities: This is like whacking the mole – you want to fix the vulnerability as quickly and effectively as possible. It’s like whacking that pesky mole before it can cause any more damage.
- Verify remediation: This is like checking to make sure the mole is really gone – you want to make sure the vulnerability has been successfully fixed and is no longer a threat. It’s like making sure you really whacked that mole and it’s not just hiding.
- Monitor for new vulnerabilities: This is like keeping an eye out for new moles that might pop up – you want to continually monitor for new vulnerabilities and address them as they arise. It’s like being on mole patrol and making sure none of those sneaky critters get past you.
Conclusion
Well, folks, we’ve reached the end of our vulnerability management journey. We’ve covered a lot of ground, from the basics of vulnerability management to the best practices for keeping your system secure.
So, what’s next? Well, we encourage you to act and implement a vulnerability management process in your organization. And if you’re feeling overwhelmed, don’t worry – Beyond Key is here to help.
At Beyond Key, we have extensive experience in vulnerability management and can help you implement an effective process that meets your unique needs. Our team of experts can provide you with the tools and guidance you need to stay on top of potential security threats and keep your system safe and secure.
So, what are you waiting for? Contact Beyond Key today for a vulnerability management assessment or to schedule a consultation. Let’s work together to keep your business safe and secure!