What Is The Primary Goal Of Penetration Testing
As a CEO or organizational decision-maker, you know that cyber threats are a growing concern for businesses of all sizes. Hackers are constantly evolving their tactics, and it can be difficult to keep up with the latest vulnerabilities and attack vectors.
That’s why penetration testing should be at the top of your security to-do list. In this blog post, we’ll explore the primary goal of penetration testing and why it’s so important for businesses to invest in this critical security practice.
But first, let’s start with a quick refresher on what penetration testing actually is. Put simply, it’s a simulated attack on your company’s systems and networks, designed to identify weaknesses that could be exploited by real hackers. By conducting regular penetration testing, you can proactively discover vulnerabilities before they are exploited by bad actors and take steps to strengthen your security posture.
Now that we’ve covered the basics, let’s dive into why penetration testing should be a top priority for your business.
The Primary Goal of Penetration Testing
Ah, the primary goal of penetration testing. It’s like going on a first date with your own company’s security systems: you’re looking for vulnerabilities, hoping to find none, but mentally preparing yourself for the worst.
Jokes aside, the main goal of penetration testing is to identify security weaknesses before they can be exploited by real hackers. By simulating an attack, penetration testing can provide a realistic assessment of your security posture and help you take proactive steps to strengthen your defenses.
But the benefits don’t stop there. Regular penetration testing can also help reduce the risk of data breaches, improve your overall security posture, and increase customer trust. And let’s be real, who doesn’t want to be known as the company that takes data security seriously? It’s like being the cool kid at the party who’s always got a backup plan in case things go wrong.
So, in short, the primary goal of penetration testing is to protect your business and your customers from cyber threats. By taking a proactive approach to security and identifying vulnerabilities before they can be exploited, you can sleep soundly at night knowing that you’ve done everything in your power to keep the bad guys at bay.
How Penetration Testing Works
Have you ever wondered how penetration testers find those pesky vulnerabilities lurking in your company’s systems? Do they have some kind of hacker superpower? Do they possess the ability to talk to computers in binary code?
Well, wonder no more. The truth is that penetration testing is a rigorous process that involves a lot of hard work and some seriously cool tools. Let’s take a closer look.
First off, there are different types of tests that may be performed depending on your organization’s needs. These can range from basic vulnerability assessments to more complex social engineering attacks that involve tricking employees into revealing sensitive information. But don’t worry, your friendly neighborhood penetration testers will work with you to determine the best approach for your organization.
Once the scope of the test has been defined, the fun begins. Penetration testers use a variety of tools and techniques to identify vulnerabilities in your systems and networks. These can include everything from port scanners and vulnerability scanners to password-cracking tools and custom scripts. It’s like being a high-tech detective, but instead of solving crimes, you’re preventing them.
Of course, it’s important to note that not all penetration testing teams are created equal. You’ll want to work with an experienced and qualified team that understands your organization’s unique needs and has a track record of success. Think of it like hiring a team of security ninjas to protect your business.
The ROI of Penetration Testing
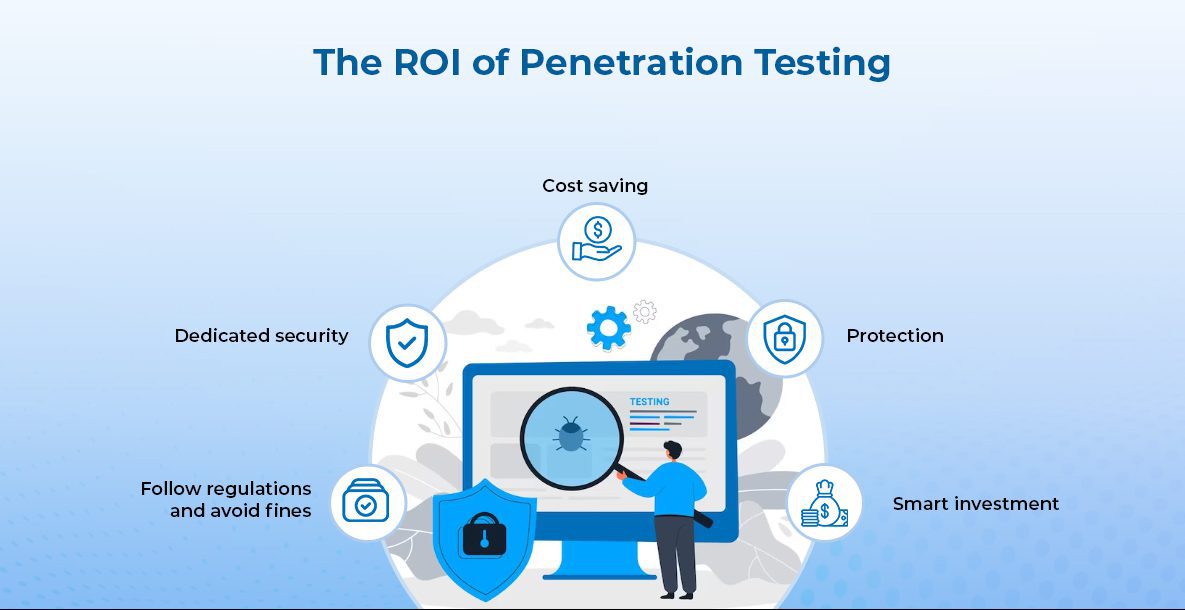
- The potential cost savings from penetration testing are so high, you’ll be able to afford a round of drinks for the security team. (Just don’t let them get too tipsy and start hacking into the wrong systems.)
- Penetration testing is like buying insurance for your business, except instead of protecting your car, you’re protecting your data. So the next time your boss complains about the cost, just remind them that a data breach would be way more expensive than a fender bender.
- Hiring a team of security ninjas to hack into your own systems may sound crazy, but it’s actually one of the smartest investments you can make. Think of it as hiring a group of professional burglars to break into your house and tell you where the weak spots are. (Just don’t forget to change the locks afterward.)
- Regular penetration testing can also help you comply with regulatory requirements and avoid costly fines. It’s like studying for a test, except instead of getting an A, you get to keep your money.
- And finally, let’s not forget the most important benefit of penetration testing: you get to tell everyone you hired a team of security ninjas. It’s like having your own personal army of cyber warriors. (Just try not to let it go to your head.)
Best Practices for Penetration Testing
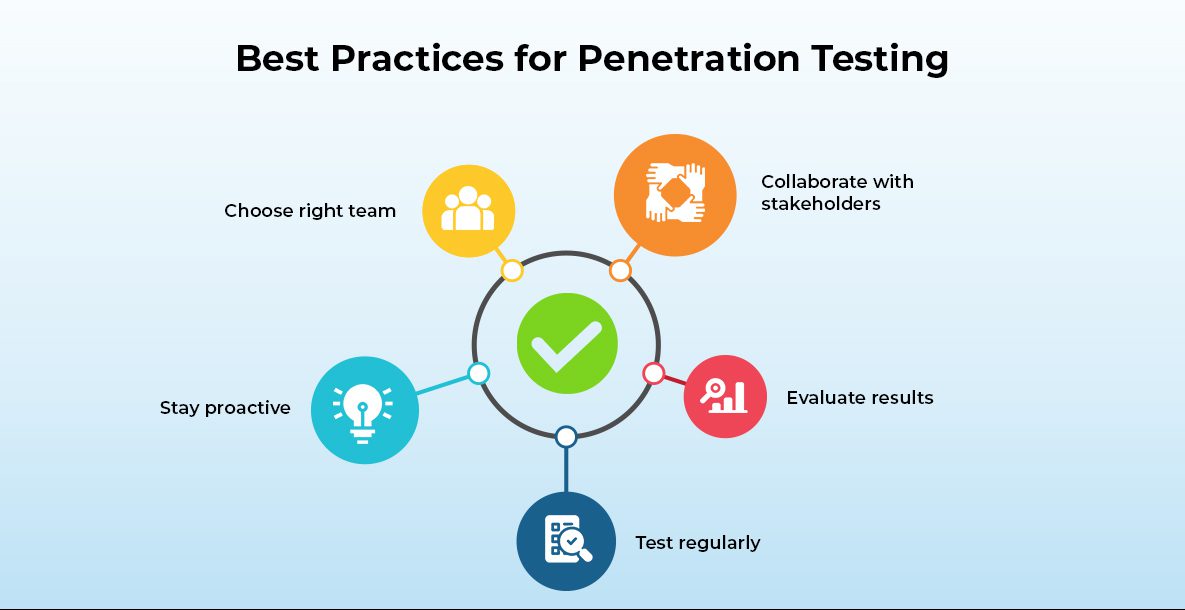
So you’ve decided to take the plunge and hire a team of security ninjas to hack into your own systems. But before you start handing over your passwords, there are a few best practices to keep in mind.
- Choose the Right Penetration Testing Team: Make sure to select a team with experience in your industry and a proven track record of success. Ask for references or case studies to verify their claims.
- Collaborate with Internal Stakeholders: Penetration testing should be an ongoing partnership between the testing team and IT, security, and management. Work together to identify vulnerabilities, prioritize remediation efforts, and align your security program with business goals.
- Use Results to Improve Security Posture: After the testing is complete, analyze the findings for patterns and use them to inform your security strategy going forward. Celebrate each vulnerability you patch as a step towards a more secure future.
- Don’t Treat Penetration Testing as a One-and-Done Exercise: Regular testing and collaboration with your team can help you stay one step ahead of the bad guys.
- Remember the Importance of Penetration Testing: Penetration testing is a critical component of any comprehensive security program. By following best practices and staying proactive, you can help protect your company from cyber threats and potentially become the hero of your own hacker movie.
Penetration testing is a critical component of any comprehensive security program. By following best practices like choosing the right team, collaborating with internal stakeholders, and using the results to inform your security strategy, you can stay one step ahead of the bad guys. And who knows, maybe someday you’ll be the hero of your own hacker movie.
Why Choose Beyond Key’s VAPT Service
Let’s cut to the chase, folks. Cybersecurity is a serious business. You can’t just hope for the best and expect the bad guys to play fair. That’s where Beyond Key’s VAPT service comes in.
It’s like having a team of ninja hackers who can find the weak spots in your systems before the real hackers do. And trust me, you want to find those weak spots before they do, because once they’re in, it’s like trying to get rid of a pesky raccoon in your attic.
So why choose Beyond Key’s VAPT service? Well, for starters, they know their stuff.
They’ve been around the block for over a decade, and they’ve got a team of certified ethical hackers who know how to think like the bad guys. Plus, they don’t just find the problems and leave you to fend for yourself. They’ll work with you to fix them and make sure your systems are locked up tight.
Sure, you might be thinking, “But won’t it cost an arm and a leg?” Not even close. It’s a small price to pay compared to the cost of a data breach. And with Beyond Key’s VAPT service, you can sleep soundly knowing you’re doing everything possible to prevent it.
Don’t wait for the bad guys to make a move. Head over to Beyond Key’s VAPT page and check it out. Because when it comes to cybersecurity, you can never be too careful.
Conclusion
In conclusion, penetration testing is like putting on sunscreen before heading to the beach. It helps identify vulnerabilities before attackers can exploit them and protect your company’s “skin” from harmful cyber rays.
Failing to invest in basic security measures is like going to the beach without any sunscreen – you’re bound to get burned and have a hard time explaining to your board why you didn’t take the necessary precautions.
So, choose Beyond Key and make sure to slather on some cyber protection and stay safe out there!