Web Application Penetration Testing: A Comprehensive Guide
Web applications are essential in today’s digital world, as they facilitate communication and collaboration between individuals and organizations. Unfortunately, the security of these applications is becoming more and more crucial due to the rise of cyber threats.
Web application penetration testing is one of the best ways to see if a web application has flaws. This blog will serve as an all-encompassing resource for learning everything there is to know about web application penetration testing, from the basics to advanced techniques.
Web Application Penetration Testing Procedures:
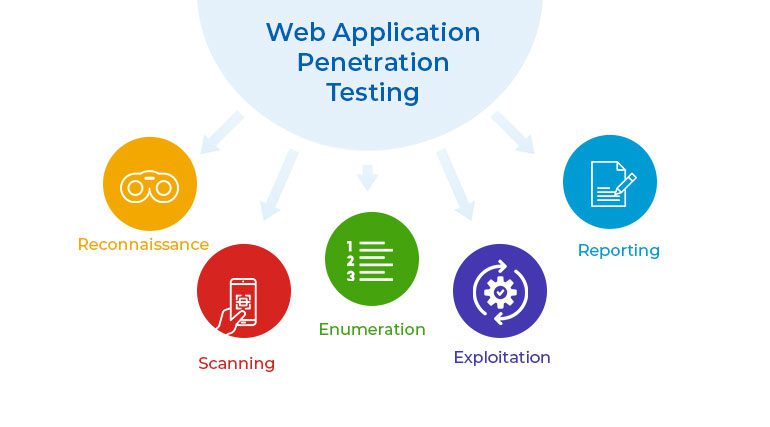
A web application penetration testing process is used to identify and evaluate security vulnerabilities in a web application. Simulating an attack from the attacker’s point of view, it lets businesses see how their web application would work in a realistic attack scenario. Web Application Penetration Testing consists of the following procedures:
Reconnaissance: Web application penetration testing starts with reconnaissance, where the tester learns about the web application being tested. This information is available through channels that anyone can use, such as the organization’s website and social media accounts. The goal is to find out as much as possible about the target web application, such as how it is built, what parts it has, and what technologies it uses.
Scanning: The tester uses scanning tools to identify vulnerabilities in the targeted web application in the following step. In this phase, automated tools like vulnerability scanners are often used to find common security flaws like SQL injection, cross-site scripting, and cross-site request forgery.
Enumeration: Enumeration is the process of interacting with a target web application to learn more about it. To identify hidden features and settings, the tester employs a variety of strategies, including URL manipulation and error message analysis.
Exploitation: After vulnerabilities are found, people try to take advantage of them. The tester uses a variety of tools and methods to get private data or take control of the target web application.
Reporting: Web App Penetration Testing ends with a report, in which the tester describes what happened during the test and makes suggestions for how to fix any problems that were found. In the report, there should be a list of all the weaknesses found, along with the risks they pose and possible solutions.
For Web Application Penetration Testing, you need security experts with the right skills. Organizations should also make sure that testing is done in a safe and controlled environment so that it doesn’t hurt the production environment.
By taking the steps above, organizations can improve the security of their web applications and take preventative steps to stop security breaches.
Techniques for Web Application Penetration Testing:
Checking the validity of the input Input validation is the process of checking user-provided data to make sure it is formatted correctly and only has the characters that are expected.
Testers do input validation testing, in which they try to get around the system’s built-in protections, to find any flaws that could be exploited. This could mean trying to send malicious data, like SQL injection or cross-site scripting (XSS) payloads, to the web application to see if it is vulnerable.
Before giving users access to private information or systems, they must prove who they are. To test authentication, you have to act out real-world situations in which an attacker tries to get into protected resources without permission.
Attempts to guess or crack passwords, take advantage of authentication vulnerabilities, or dupe users into disclosing their credentials are all examples of authentication attacks.
The testing of session management entails ensuring that user sessions and the data associated with them are properly tracked and managed. The goal of session management testing is to use flaws in the session management process to get unauthorized access to sensitive data or functions. The attacker could go after sessions that are already going on, change session identifiers, or try to stop sessions from ending.
Access control testing means making sure that only people who are allowed to can see private information and use private features. In order to gain unauthorized entry to private information or restricted features, testers perform “access control testing.”
This includes things like trying to use features or data that are only available to certain users or roles or changing access control data to get around those limits.
Evaluation of the Security of Cryptographic Systems and Protocols Used to Protect Sensitive Data is Known as Cryptographic Testing. During cryptographic testing, an attacker acts out a situation where they try to break the system or protocols in use by taking advantage of weaknesses.
Some examples of this kind of attack are attempts to decrypt data encrypted with a different key, misuse of cryptographic keys, and vulnerabilities in cryptographic algorithms.
These are some of the most important techniques used in web application penetration testing to check how safe a web application is. By finding and fixing vulnerabilities in these places, organizations can improve the security of their web applications and reduce the risk of data breaches and other security problems.
Web Application Penetration Testing Benefits
There are many compelling arguments in favor of performing Web Application Penetration Testing. Web applications are complex systems that may have a wide variety of security flaws that need to be discovered.
Web Application Penetration Testing is a good way to find these weaknesses and understand how an attack works. Businesses need to do regular security audits of their web applications to show that they are following the rules in many fields.
Web App. Penetration Testing can help businesses meet these requirements and show that they are following the rules. Web applications often store and process sensitive data, such as personal information, financial information, and trade secrets.
Organizations can use Web Application Penetration Testing to identify and fix any vulnerabilities that could be used to gain access to or compromise this private information.
Web Application Penetration Testing is a way for organizations to improve their security and lower the risk of a security incident. Some examples of this are better configuration management and the creation and use of security policies and procedures.
Organizations can gain the trust of their customers and other stakeholders by showing they care about security and doing regular Web Application Penetration Testing. This can help both the brand’s reputation and the number of people who buy it.
The advantages of Web Application Penetration Testing are numerous, and these are just a few of them. By testing the security of their web applications regularly, organizations can stay in line with regulations, protect sensitive information, improve their security, and win over customers and other stakeholders.
Why hire a consultant to do something that you can do yourself?
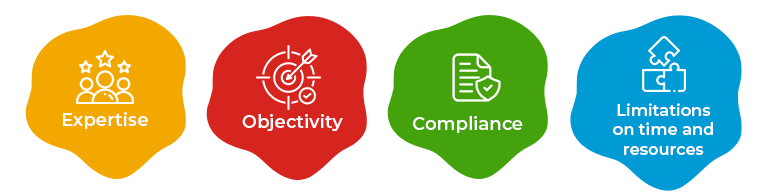
Organizations may decide to hire a consultant for web application penetration testing for a number of reasons, such as:
Expertise: Testing the security of a Web application can be hard and requires a lot of knowledge. Hiring a consultant with the right experience can make the testing go more quickly and well.
Objectivity: A third-party consultant can give a company’s web application security an unbiased evaluation. This can help internal security teams find any blind spots or places they may have missed.
Compliance: Hiring a consultant can help a business follow web application security rules and show auditors and other important people that they are following the rules.
Limitations on time and resources: A thorough web application penetration test can take a lot of time and work. Companies can avoid putting too much stress on their own teams by hiring consultants to do the testing in a timely and effective way.
These are just a few of the many good reasons why a business might decide to hire a web application penetration testing consultant for Penetration Testing Services.
Conclusion
Web application penetration testing is necessary to ensure that web apps are safe. Many businesses rely heavily on applications like these to store and process sensitive data, give access to essential business systems and services, and serve as the main point of contact between the company and its customers and users. Regularly checking web applications’ security is essential to ensure they are safe from threats.
Web App. Penetration Testing aims to find security holes in web apps and take advantage of them. Attackers can use these flaws to get unauthorized access to data, stop services from working, or get into the system itself.
These holes can be caused by simple configuration problems or more complicated software flaws. When organizations do web application penetration testing, they can find these flaws and fix them before attackers use them.
By working with an experienced consultant, someone like Beyond Key, your company can make sure that its web applications are thoroughly tested and that any flaws are found and fixed quickly and effectively.